Ransomware malware can be spread through malicious email attachments, infected software apps, infected external storage devices and compromised websites. A growing number of attacks have used remote desktop protocol and other approaches that don't rely on any form of user interaction.
In a lockscreen variant of a ransomware attack, the malware may change the victim's login credentials for a computing device; in a data kidnapping attack, the malware may encrypt files on the infected device, as well as other connected network devices.
While early instances of these attacks sometimes merely "locked" access to the web browser or to the Windows desktop -- and did so in ways that often could be fairly easily reverse-engineered and reopened -- hackershave since created versions of ransomware that use strong, public-key encryption to deny access to files on the computer.
Famous ransomware: CryptoLocker and WannaCry
Perhaps the first example of a widely spread attack that used public-key encryption was Cryptolocker, a Trojan horse that was active on the internet from September 2013 through May of the following year. The malware demanded payment in either bitcoin or a prepaid voucher, and experts generally believed that the RSA cryptography used -- when properly implemented -- was essentially impenetrable. In May 2014, however, a security firm gained access to a command-and-control server used by the attack and recovered the encryption keys used in the attacks. An online tool that allowed free key recovery was used to effectively defang the attack.
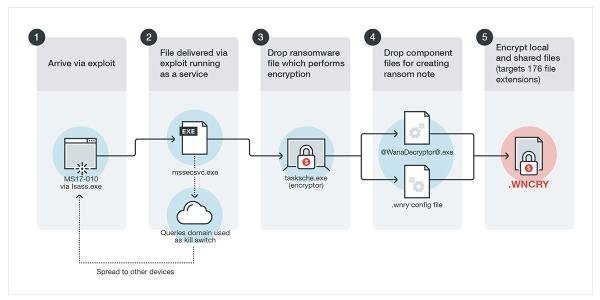
In May 2017, an attack called WannaCry was able to infect and encrypt more than a quarter million systems globally. The malware uses asymmetric encryption so that the victim cannot reasonably be expected to recover the (private and undistributed) key needed to decrypt the ransomed files.
Payments were demanded in bitcoin, meaning that the recipient of ransom payments couldn't be identified, but also meaning that the transactions were visible and thus the overall ransom payments could be tallied. During the thick of the week in which WannaCry was most virulent, only about $100,000 in bitcoin was transferred (to no avail: There are no accounts of data having been decrypted after payment).
The impact of WannaCry was pronounced in some cases. For example, the National Health Service in the U.K. was heavily affected and was forced to effectively take services offline during the attack. Published reports suggested that the damages caused to the thousands of impacted companies might exceed $1 billion.
According to the Symantec 2017 Internet Security Threat Report, the amount of ransom demanded roughly tripled from the previous two years in 2016, with the average demand totaling $1,077. Overall, it's difficult to say how often these demands are met. A study by IBM found that 70% of executives they surveyed said they'd paid a ransomware demand, but a study by Osterman Research found that a mere 3% of U.S.-based companies had paid (though percentages in other countries were considerably higher). For the most part, payment seems to work, though it's by no means without risk: A Kaspersky Security Bulletin from 2016 claimed that 20% of businesses that chose to pay the ransom demanded of them didn't receive their files back.
As of 2015, there is also mobile ransomware. A malicious Android app called Porn Droid locked the user's phone and changed its access PIN number, demanding a $500 payment.
Internet of things ransomware may not be far behind. Two researchers, Andrew Tierney and Ken Munro, demonstrated malware that attacked, locked and demanded a one-bitcoin ransom on a generally available smart thermostat at the 2016 Def Con conference.
How ransomware works
Ransomware kits on the deep web have allowed cybercriminals to purchase and use a software tool to create ransomware with specific capabilities and then generate this malware for their own distribution and with ransoms paid to their bitcoin accounts. As with much of the rest of the IT world, it's now possible for those with little or no technical background to order up inexpensive ransomware as a service (RaaS) and launch attacks with very little effort. In one RaaS scenario, the provider collects the ransom payments and takes a percentage before distributing the proceeds to the service user.
Attackers may use one of several different approaches to extort digital currency from their victims. For example:
- The victim may receive a pop-up message or email ransom note warning that if the demanded sum is not paid by a certain date, the private key required to unlock the device or decrypt files will be destroyed.
- The victim may be duped into believing he is the subject of an official inquiry. After being informed that unlicensed software or illegal web content has been found on his computer, the victim is given instructions for how to pay an electronic fine.
- The attacker encrypts files on infected devices and makes money by selling a product that promises to help the victim unlock files and prevent future malware attacks.
- In an interesting reversal, the extortion may be made with the threat not so much that the data will be unavailable (though this may also be the case), but that the data will be exposed to the general public in its unencrypted state if the ransom is not paid by a given deadline.
Ransomware prevention
To protect against ransomware attacks and other types of cyberextortion, experts urge users to back up computing devices on a regular basis and update software -- including antivirus software -- on a regular basis. End users should beware of clicking on links in emails from strangers or opening email attachments. Victims should do all they can to avoid paying ransoms.
if someone looking for how to make ransomewhere & proceed,
Contact us : https://www.facebook.com/blackhathacking123/
Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com
Hack into Paypal accounts, B logs,Professional hacking into institutional servers-keylogging -University grades
ReplyDeletechanging / Admin(staff) account hack -Access/Password (Facebook, Instagram, bbm,Skype, snap chat, twitter, badoo, Word Press,zoosk, various blogs, icloud, apple accounts etc.)-You can also learn some basic shit you wouldn't think you'd need on your everyday basis but find out how important and helpful they really are. use random credit cards to shop online, hack iphones, tap into your friends cal and monitor conversations, email and text message interception
Contact: ( hackingsetting50@gmail.com) for any hacking jobs